GitOps as an Operating Model: Running Kubernetes at Scale with Helm and CI/CD
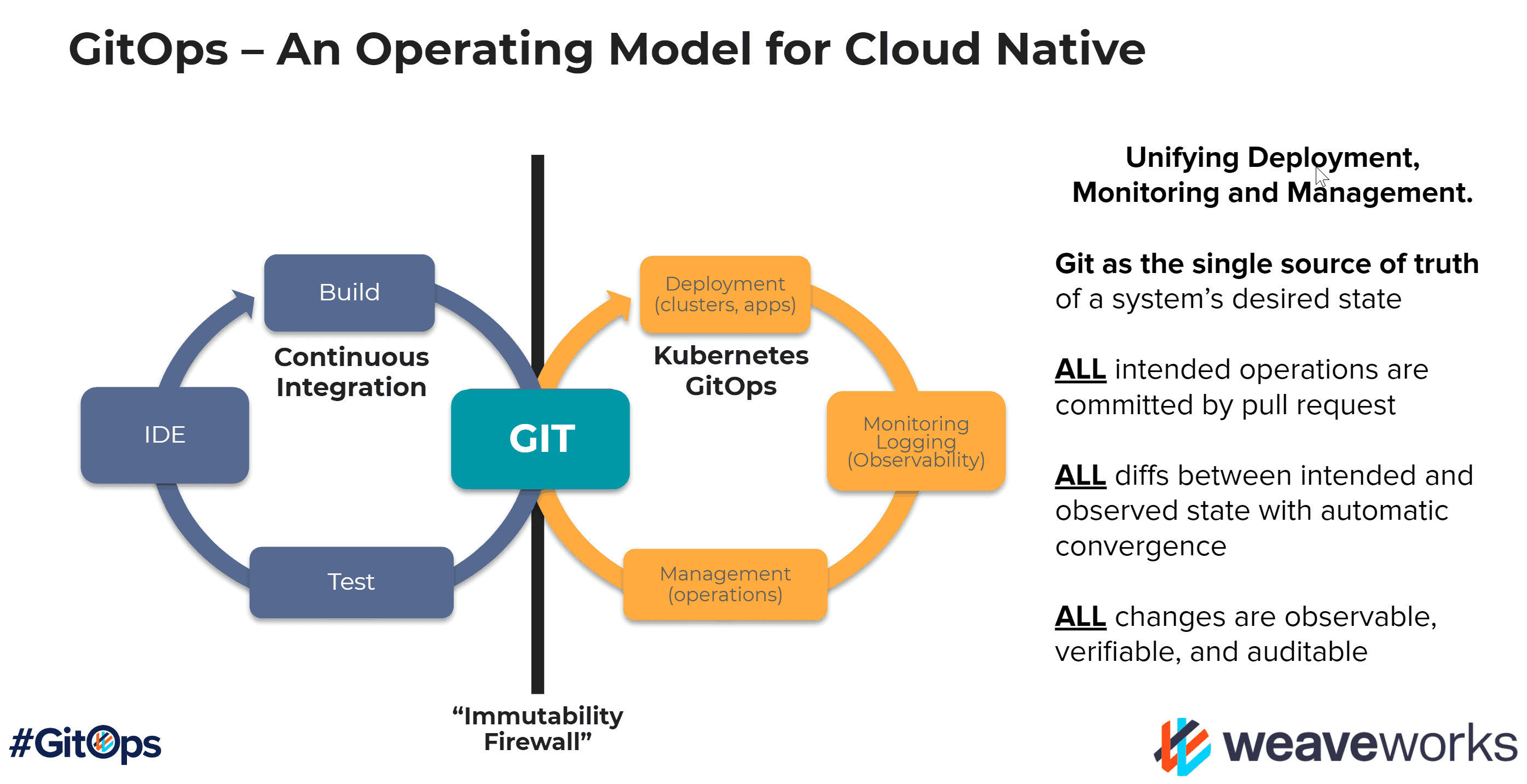
GitOps Is Not a Tool - It's a Contract
Most teams adopt GitOps for deployments. Senior teams adopt it for control, auditability, and safety.
GitOps answers hard questions:
- Who changed what?
- When did it change?
- Why did it change?
- How do we undo it safely?
Operating Model
Git (Desired State)
|
|-- Pull Requests (Human Control)
|
CI / CD (Policy Enforcement)
|
Kubernetes (Reconciled State)
There is no imperative access to production.
Repository Design (Optimized for Humans)
application-platform/
├── charts/
│ └── api-service/
├── environments/
│ ├── dev.yaml
│ ├── uat.yaml
│ └── prod.yaml
├── policies/
│ └── resource-limits.yaml
└── pipelines/
Key Rule
If it runs in prod, it must exist in Git.
Helm as a Packaging Boundary
apiVersion: apps/v1
kind: Deployment
metadata:
name: {{ .Release.Name }}
spec:
replicas: {{ .Values.replicas }}
strategy:
type: RollingUpdate
Helm is not used for templating convenience - it's used to enforce consistency across teams.
Environment Configuration Is Explicit
replicas: 4
resources:
limits:
cpu: "1000m"
memory: "1Gi"
autoscaling:
enabled: true
Production differs by design, not accident.
CI/CD Pipeline as a Policy Engine
deploy:
stage: deploy
script:
- helm lint charts/api-service
- helm upgrade --install api charts/api-service -f environments/prod.yaml
This is where:
- Security scans run
- Policy checks happen
- Rollouts are controlled
Why This Scales Organizationally
- Developers ship faster
- Platform teams sleep better
- Auditors get Git logs
- Rollbacks are predictable
Most importantly: production becomes boring again.
Final Thoughts
- Terraform defines what exists
- Kubernetes defines how it runs
- GitOps defines who controls it
A platform succeeds not when it's powerful - but when it's predictable under failure.
Enjoyed this architecture deep-dive?
Discuss Platform Engineering